Let us define Ransomware
Ransomware is a computer virus that infects the computer with the sole intention of extorting money from victims. Its objective is to make the common file unreadable so that it can justify the request for ransom payment in order to restore the data to its original form. This kind of virus is considered a cybercrime that can infiltrate the computer through deceptive links and malicious file downloads.
More about Ransomware
This kind of malicious software or malware is clever in restricting users’ access to their computer or personal data, such as documents, images, photos, videos, and similar items. The denial of access to the device or files will persist until you are forced to pay the requested amount. The usual payment scheme for this kind of attack is often Bitcoin cryptocurrency. Aside from being a profitable currency, using this channel of payment makes it hard for authorities to track down the offenders.
Ransomware is a form of cyber-blackmailing tactics used by online criminals and is considered one of the most dangerous types of computer viruses today. It is spreading rapidly worldwide at an enormous speed using various deployment vectors like spam emails, pirated software, infected websites, malicious advertisements, or fake software updates being pushed by online ads.
With different variants of ransomware being developed, the number of computer users being infected with this virus keeps growing along with the creation of new versions or modified models for a much more hazardous payload. Other ransomware was just recycled from the older variants but seemingly powered by a new set of codes and a much more complex cipher. This cycle of ransomware makes it a constantly growing threat that puts computer users’ security in jeopardy.
What are the types of ransomware?
There are two types of ransomware that are widely spread over the internet. They are Locker and Crypto ransomware. They may be different in methods, but they share the same objective of extorting money from innocent victims.
Locker Ransomware
This type of virus blocks the user’s access to the device or basic computer functions. Some Locker ransomware may appear at the boot level of computers, while others will let the user enter the Windows OS screen but deny access to the log-in screen or program operation. Hence, the most influential ones are those that claim to be from the FBI or government entities claiming to have found illicit objects on the computer.
Crypto Ransomware
On the other hand, crypto ransomware like DJVU, Xorist, Dharma, HiddenTear, and similar types were developed to encrypt data on the computer, especially crucial files like documents, photos, images, videos, and so on. Victims were threatened that their data would be permanently encrypted or destroyed unless a fee was transmitted to the designated payment channel. The bulk number of Crypto ransomware targets ordinary computer users. Hence, there is an observation about the steady growth of attacks on corporations, offices, and institutions such as government, universities, and the health sector.
How do I prevent ransomware infections?
It is not really difficult to avoid ransomware-type infections. In fact, the majority of victims are just a tiny percentage of overall computer users globally. Normally, those who are careless when using the internet often fall victim to this dreaded virus. To prevent the infection, we prefer to provide these computer security practices to protect against all sorts of virus attacks.
- Always download and install system patches or updates for the operating system to make sure that the latest security modules are applied to the computer.
- Update every program on the computer as necessary. Be sure to download the software update from official sites and legitimate sources.
- Avoid downloading pirated software and freeware that are being offered by suspicious websites. As much as possible, obtain any particular apps from official websites.
- Be sure to protect the computer with effective anti-virus or anti-malware tools. These programs are useful in automatically detecting the threat and, thus, thwarting the potential infection.
- Lastly, run a file backup routine. This may not help in preventing the ransomware attack, but it ensures file safety just in case the virus penetrates the computer and manages to encrypt the data.
One important step before proceeding with the procedures below is to backup your files. Ransomware is not the same. Each has its own unique set of payloads, aside from encrypting the files with a complex method. Others tend to delete the infected files after a certain period, while others keep them concealed in hidden places. In addition, ransomware decryption tools are not guaranteed to be perfect, and there are instances where files suffer damage during the decryption process. So, create a backup copy of your entire encrypted file right now.
How to Remove Ransomware
The first thing to do is to remove the ransomware before attempting the decryption. Remember that as long as the ransomware is active, it will repeatedly encrypt the files on the compromised computer.
Quick Fix - Scan the PC with Combo Cleaner for Windows
Combo Cleaner is a trusted PC security and optimization tool equipped with powerful virus and malware detection engine. This program can get rid of browser hijacker, adware, and malware.
1. Download the application from the following page:
2. Save the file to your preferred location.
3. Double-click the downloaded file CCSetup.exe and install with the default settings.

4. At the end of the setup process, click Finish to run Combo Cleaner.
5. The tool will update the signature file, please wait for this process to complete.
6. To begin checking for threats like browser hijacker, adware, and malware, click on the Start Scan button. Wait for this scan to finish.

7. At the end of the scan process, click on Remove all threats to delete threats including all malicious objects from the computer.
Free features of Combo Cleaner for Windows includes Disk Cleaner, Big Files finder, Duplicate files finder, and Uninstaller. To use antivirus, privacy scanner, and to delete identified threats, users have to upgrade to a premium version.
Please continue with the succeeding removal procedures if your are comfortable to manually get rid of the threat and malicious items linked with it.
Stage 1 : Temporarily Disable System Restore on Windows OS
Because ransomware and relevant viruses are capable of reinstating themselves by exploiting the System Restore of Windows, we suggest that you temporarily disable System Restore while executing the steps. This option is also helpful to effectively run a full scan on the computer.
Do not forget to re-enable System Restore after completing the removal of ransomware. This feature is vital in reinstating the operating system to its previous normal working condition in the event of arising problems or conflicts.
Infection by the ransom virus is dangerous to the system because it can inject files that run each time Windows starts. To prevent malicious files from loading, the Windows operating system must run with minimal processes, and this can be done through SafeMode with Networking.
Stage 2 : Start Windows in Safe Mode With Networking
The method of running Windows in Safe Mode before running a virus scan is effective in getting rid of malware. This process can prevent most viruses and malware from loading, making it easier to detect and remove them.
1. On the Windows Search bar, please type msconfig.

2. Select and open System Configutation on the list of found results.
3. Once you are in the System Configuration window, go to the Boot tab.

4. Under the Boot Options area, please check Safe Boot and select Network. This will allow Windows to boot in Safe Mode with Networking.
5. Lastly, click on Apply and OK to save the changes.
6. Please restart Windows.
Do not forget to restore the normal boot process of Windows after running the virus scan. Simply repeat the method above, and this time, uncheck the Safe Boot option to run Windows normally.Stage 3 : Scan the Computer with Malware Removal Tool
Ransomware files are placed deeply into the system and in various locations, thus, thorough scanning is vital to totally removing the ransomware. Aside from our suggested tool, you may also run your own security program.
To remove the ransomware automatically, scanning the computer with this efficient anti-malware tool is suggested. This scanner does not just uncover known threats like viruses or malware, it is also effective in discovering hazardous ransomware.
1. Download Sophos Virus Removal Tool from the link below. Save the file on your computer where you can easily access it.
2. Once the download completes, browse the location of the file. Double-click to run the program and begin the install process.
3. On the first window of the installation wizard, click Next to continue. Then, it will display the program’s License Agreement. You need to Accept the terms in order to proceed. If Windows prompts for User Account Control, please click Yes to proceed.
4. On succeeding windows, click Next or Continue to carry on with the installation. After completing the installation process, Launch Sophos Virus Removal Tool.
5. An Internet connection is required when running this virus scanner in order to download important updates. Make sure that everything is up-to-date to effectively remove the ransomware and other relevant viruses.
6. Click the Start Scanning button to inspect the computer. This will check the system for the presence of malicious objects, malware, and viruses. The tool reveals items that were found linked to the ransomware and other suspicious entities. Be sure to remove all identified threats.
The above procedures should have totally eliminated the ransomware. However, if you find that there are still remnants of the virus, please proceed to the next steps below.
Recover Files from Ransomware Infection
Decrypting infected files with Emsisoft Tools
This service from Emsisoft is helpful in unlocking encrypted files without paying a ransom. It gives three ways to detect the ransomware and provides a suitable recovery method:
Upload ransom note – This is usually the .txt or .hta file that was generated by the ransomware.
Upload the encrypted file – The actual encrypted file. Choose the one that is less than 8MB in size.
Contact information – Enter the email address or any links provided as they appear in the ransom note.
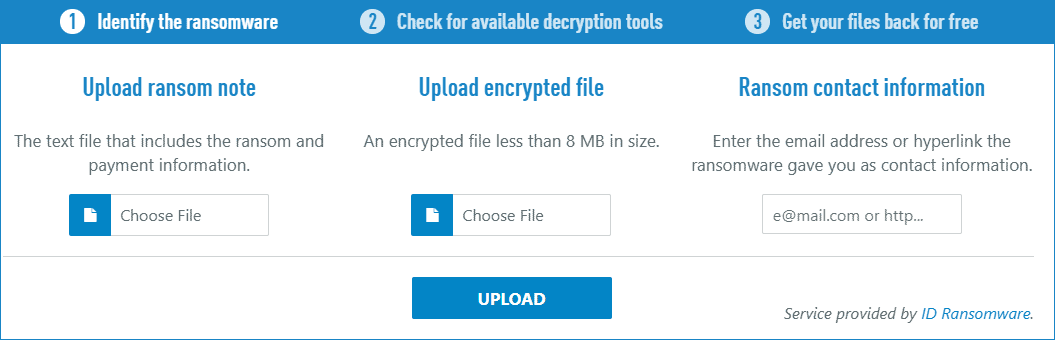
After submitting any of the appropriate data, Emsisoft will attempt to identify the ransomware and provide keys if there are available.
Option: Use ShadowExplorer to restore files encrypted by Ransomware
ShadowExplorer takes advantage of shadow copies created by Windows. This tool allows you to retrieve older versions of files before they were encrypted by ransomware.
1. Download ShadowExplorer from the official web site.
2. Install the program with the default settings.
3. The program should run automatically after installation. If not, double-click on ShadowExplorer icon.
4. You can see the drop-down list on top of the console. Please select the proper drive and the most recent point-in-time shadow copies of files you wish to restore prior to ransomware infection.

5. Right-click on the Drive, Folder, or File you wish to restore and click Export…
6. Lastly, ShadowExplorer will prompt for the location where you want to save the recovered files.

